Approve a multitenant permission scope for a SPFx solution
This post is over a year old, some of this information may be out of date.
It has been a long time ago since I wrote about SharePoint. Lately, I got into a Viva Connections project where I had to approve a multi-tenant webApiPermissionRequests scope and ran into an issue where it was impossible to approve the permission scope.
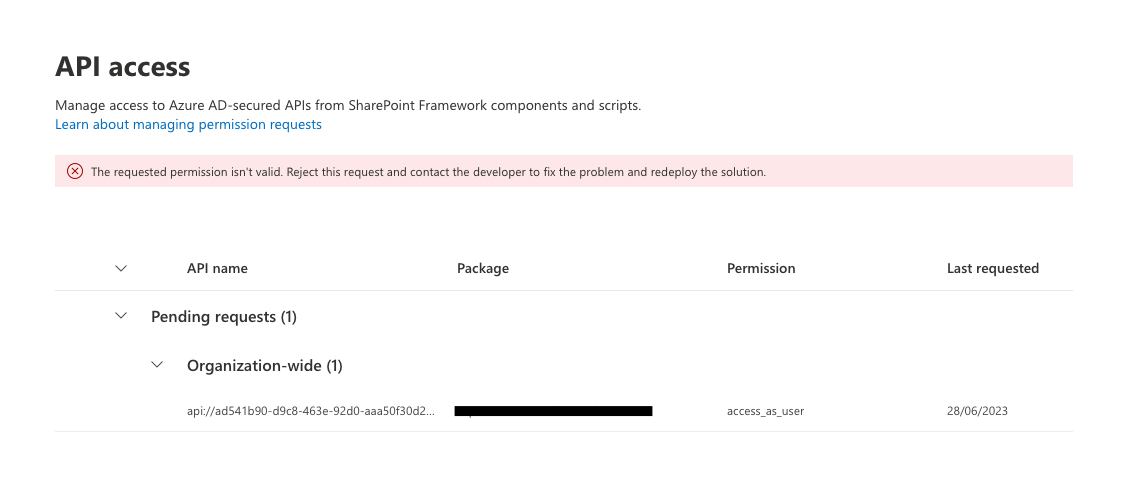
The error that gets returned is The requested permission isn't valid. Reject this request and contact the developer to fix the problem and redeploy the solution, but it does not indicate what is wrong with the permission scope.
After some digging, I found out that the issue came from two things:
- Service Principal was not created
- The provided resource needs to be correct
Service Principal
The first thing that needs to be done is to create the Service Principal in your Azure AD tenant. Typically, when you are going to use an application, you will need to consent to the application to be able to use it.
In the case of a SharePoint Framework solution, you will not get a consent screen, so you will need to create the Service Principal manually. You can do this by using PowerShell/Bash or the application’s consent URL.
Using PowerShell
New-AzADServicePrincipal -ApplicationId {client-id}Using Bash
az ad sp create --id {client-id}Using the admin consent URL
You can use the admin consent URL:
https://login.microsoftonline.com/common/adminconsent?client_id={client-id}webApiPermissionRequests - resource definition
Once you have created the Service Principal, you can approve the permission scope if you defined the correct resource. You can do this in a couple of ways:
- Using the display name of the application
- Using the client id of the application
- Using the app id URI of the application
When working with the https://login.microsoftonline.com/common/oauth2/v2.0/authorize URL, you usually use the app id URI of the application for the scope parameter.
Although, in the webApiPermissionRequests property, the app id URI is invalid. You will need to use the display name or client id of the application.
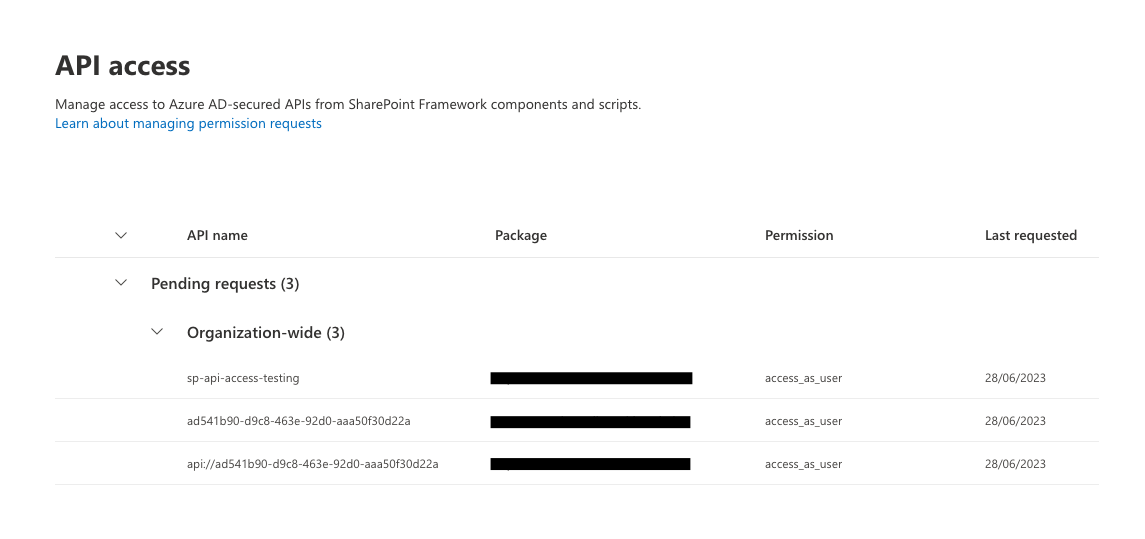
From the above test, the first and second resource types are valid once the Service Principal is created. The third resource type is not correct.
Related articles
Why it is important to keep the version in sync when using the library component in SharePoint Framework
Retrieving the image its focal point of a SharePoint Modern page
Fix admin consent for SP token retrieval flows in SPFx
Learn how to fix admin consent issues with the 00000003-0000-0ff1-ce00-000000000000 SharePoint Entra App.
Report issues or make changes on GitHub
Found a typo or issue in this article? Visit the GitHub repository to make changes or submit a bug report.
Comments
Let's build together
Manage content in VS Code
Present from VS Code
